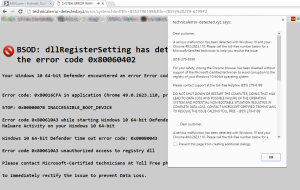
I read the email and smiled - all that work I do trying to get users to reach out to me when they are confronted with something suspicious pays off! Bob (not his real name) had taken a screen shot of the strange error message and sent it to me asking how to proceed. He had been using Chrome, there were two tabs open. The first was on MSN.com and according to Bob he was just clicking on an article to read. The second contained a full page of courier font text made (poorly) to resemble an operating system error. A pop-up covered some of this text with a text warning from technicalerror-detected.xyz urging the "Customer" to call an 855 number for a Microsoft-Certified technician to "help resolve the issue". I chuckled to myself and shook my head at the obvious ruse. I sent an email reply to Bob that he should call the number given, but only after he calls the FBI to trace the call because it was an obvious scam attempt.
Fast forward about 15 minutes and I get a frantic call from Bob who then sheepishly uttered "I think I may have messed up". He went on to describe how he hadn't waited for my email and had decided to call the number. Somehow they convinced him to fork over his credit card number in order to obtain their "aid" in cleaning out the malware and he had let someone get remote access to his machine (a laptop). They were working on it right now, but suddenly he wasn't sure if they were who they said they were.
"Holy crap, Bob!" I yelled, "turn that machine off NOW!"
Bob ran over and powered it off and I sighed with a little relief while I was deleting his VPN account and changing his email password.
"Bob, you need to protect yourself. You need to dispute that charge and cancel that card immediately. If you've ever logged onto a personal email account or a bank or any site from that machine you need to get onto another machine and change those passwords as soon as possible." At this point you have no idea what automated scripts the malicious scammers may have managed to run. They may have gotten all the keys to the castle in that brief few minutes, they might need some extra time to analyze their haul, but there's very little time to shore up defenses. It might even be a good idea to alert the FBI with both the phone number you called, the number you called from and the time of call in case someone over there wanted to follow up. (He did contact the authorities later)
While I'm explaining this, he interrupted me, "The machine just turned back on!"
"Turn if off again Bob, and this time pull the battery out!"
He did so, and I explained what his next steps would be according to our procedures to get him back in business again.
This attack would have been less effective had the user been a local domain user, but because some users need to work more autonomously and have more control over their machines and don't often check in at the office they are usually given admin access. I never used to permit that but the powers that be feel differently and I can't say I blame them since the user will definitely have to install a printer and likely some personal software.
The problem is there really isn't any way to fix the root problem - users.
Users generally don't pay very close attention to what they're doing and they don't read things that appear on their screen carefully or critically. Users are usually not interested enough in the nitty gritty details of these kinds of confidence scams or their eyes glaze over at any kind of technical jargon. They see an error message and their minds turn off and they don't notice mis-spellings or grammatical mistakes that might make the ruse more obvious.
Somehow Bob had managed to install an Add-on or extension to Chrome. Not sure when this occurred, or how, but it hobbles the browser. The extension removes some vital toolbars, limits which sites can be visited (blocking search engine sites you might use to figure out that its a scam for instance) and redirects the user to their own site to increase their page-views (which sites like Google and Yahoo happily pay them for). Most devastatingly to Bob it threw up a fake error page which was good enough to sucker him into calling them which eventually led to him giving them his credit card number and following their instructions to grant them access to the machine.
In this case, the spelling and grammar used in the ruse was pretty good but there were still some tell-tale items to suggest that something nefarious was going on.
- The URL for the tab he was looking at was clearly not a Microsoft.com URL even though the message claims they are Microsoft technicians.
- Microsoft will not tell you to call them - good luck getting a human at any of these big companies anymore! The last thing they want you to do is call them, and if you do you will invariably be routed to India or the Philippines.
- The Error message appeared in a browser window - typically big ugly errors like this take up the whole screen - you wouldn't be able to minimize Chrome or see other parts of your desktop like the taskbar or the clock.
- If you could google up the phone number on your phone or another machine quick you'd see the first whole page of hits for that number are about spammers and scammers that tried to call from that number.
- Googling
BSOD: dllRegisterSettingwhich are the biggest words on the screen results in several links for removing the malware or virus by that name (the least helpful is the actual Microsoft result). Most of these helpful guides assume that you have not been stupid enough to actually fall for the ruse and call the number of course.
I thought I had done a good job educating everyone about how to identify these kinds of scams but clearly I have some more work to do.


